Security
-
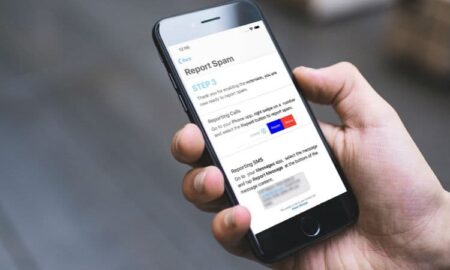
How to Block Unwanted Calls, Emails And Messages in iOS 13
How often your iPhone device gets bombarded with unnecessary calls, emails and messages? If your answer is A LOT and if you...
-
Airport USB Charging Stations Can Potentially Purloin A Lot Of Your Personal Data
Smartphone has become an essential need for almost everyone in this technological era. Subsequently, when a device is low on bars, there’s...
-
Is Pakistan’s Digital Security Protected? Senate Committee Has Serious Reservations!
On Thursday, the Senate Committee expressed strong reservations over Pakistan Telecommunication Authority’s (PTA) decision of inking a contract with a US-based firm....
-
USB Flash Drive eyeDisk Is Anything But Unhackable
If security researchers claim that a software, hardware, device or anything which they develop is unhackable, they call themselves in for a...
-
This Is How You Can Be Wary Of The Latest Phishing Method – Inception Bar
A new phishing technique has popped up and it’s known as inception bar. One of the developers Jim Fisher recently identified this...
-
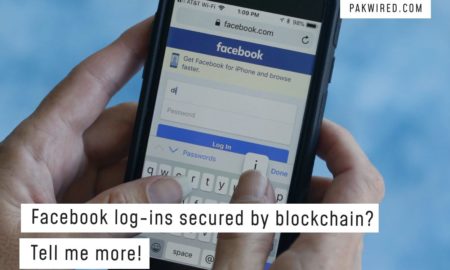
Facebook log-ins secured by blockchain? Tell me more!
The question is, even if Facebook pulls it off, will it make user data more secure or not? In an interview with...
-
You’re Still Doing Cybersecurity Wrong
Years ago, you heard about Target’s data breach, the attack on Ashley Madison and Experian’s expensive hack and thought: not me. So,...
-
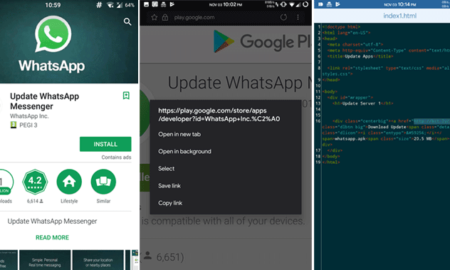
More Than Million Users Have Downloaded A Bogus WhatsApp App From Google Play Store
Google Play Store has been on the top list of many cyber criminals during the last few years as it has been...
-
Discover Bugs In The Top Android Apps And Get Paid $1,000, Google Offers
In the last few years, most of the tech companies have introduced a trend of bug bounty programs. The idea revolves around encouraging...
-
Indian Police Arrests Two Credit Card Hackers; Alleged To Have Connection With A Pakistani
On Monday, the cyber wing of Madhya Pradesh Police took into custody two individuals for their involvement in hacking credit cards of...